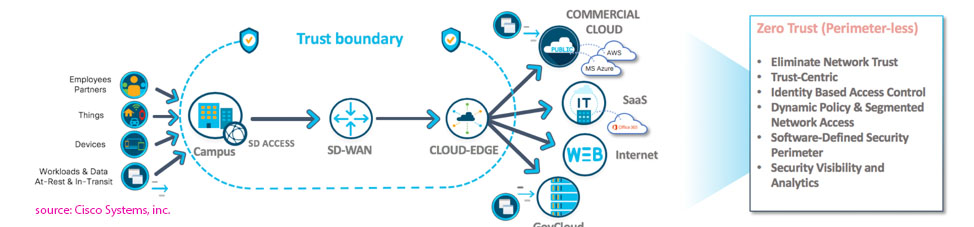
In the world of cybersecurity, the Zero-Trust Security Model has emerged as a potent strategy to protect organisations from both external and internal threats. This model operates on a straightforward principle: “Never trust, always verify,” regardless of whether the request comes from inside or outside the organisation’s network.
However, as I’ve discovered latterly when talking to capability managers and implementers there is still a large misunderstanding of what zero-trust actually is. Hence it is imperative to understand that implementing this model requires careful planning, and understanding its nuances is essential to avoid common errors and misunderstandings. This article will delve into the zero-trust model, providing examples of its implementation, and addressing some common misconceptions, unpacking the Zero-Trust Security Model in simple terms.
Understanding the Zero-Trust Security Model
The zero-trust model is a security concept centered on the belief that organisations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access.
Zero Trust is designed to protect modern digital environments by leveraging network segmentation, preventing lateral movement, providing Layer 7 threat prevention, and simplifying granular user-access control.
How to Implement the Zero-Trust Security Model
Implementing the zero-trust security model involves several key steps:
- Identify sensitive data: The first step is to identify the data that needs to be protected. This could be customer information, intellectual property, financial data, etc.
- Map the data journey: Understand how data moves across your network. Who has access to it? Where does it go? This step includes documenting data flows and identifying all assets on the network.
- Architect a zero-trust network: Use micro-segmentation to divide your network into zones, each requiring separate access permissions. This reduces the chances of an attacker moving laterally within your network.
- Create a policy for access control: Define who has access to what data, and under what circumstances, based on the principle of least privilege (PoLP). Each user should have just enough access to perform their duties.
- Deploy Zero Trust network technologies: Implementing zero-trust architecture will require a range of technologies, including multi-factor authentication (MFA), identity and access management (IAM), and encryption.
- Continuously monitor and improve: Implement security analytics to monitor network traffic and detect abnormal behavior. Regular audits and improvements to the zero-trust model are vital.
Examples of Zero Trust
Google’s implementation of its zero-trust model, known as BeyondCorp, is a prime example. BeyondCorp shifts access controls from the network perimeter to individual users and devices, allowing employees to work securely from any location without needing a traditional VPN.
Another example is the UK Government’s Digital Service, which uses a zero-trust model to allow civil servants to access work systems from anywhere, using any device. This model has been crucial during the COVID-19 pandemic when remote working became the norm.
Common Errors and Misunderstandings
Despite its advantages, several misunderstandings and errors commonly occur in the implementation of the zero-trust model:
- Perceiving Zero Trust as a product: Zero Trust is a strategy, not a single product or solution that can be purchased and installed. It is a holistic approach to network security that involves various components and a continuous commitment to monitoring and improvement.
- Underestimating the need for thoroughness: Zero Trust requires comprehensive visibility into every device, user, and network flow, which can be challenging and time-consuming to achieve.
- Overlooking the user experience: In the pursuit of security, it’s crucial not to make systems too cumbersome for users. Balancing security and user experience is key to successful implementation.
- Forgetting about internal threats: A common misconception is that zero trust is only about keeping external attackers at bay. In reality, it’s equally essential to guard against threats originating from within the organisation.
Conclusion
Adopting a zero-trust security model is an effective way to protect your organisation from today’s sophisticated cyber threats. The model’s core premise, “Never trust, always verify,” challenges traditional security models that focus on defending the perimeter. By implementing a zero-trust model, organisations can have more granular control over access to their systems and data. However, successful implementation requires thorough planning, the right technologies, and a clear understanding of the model’s principles to avoid common errors and misunderstandings to Fortifying the Digital Frontlines.