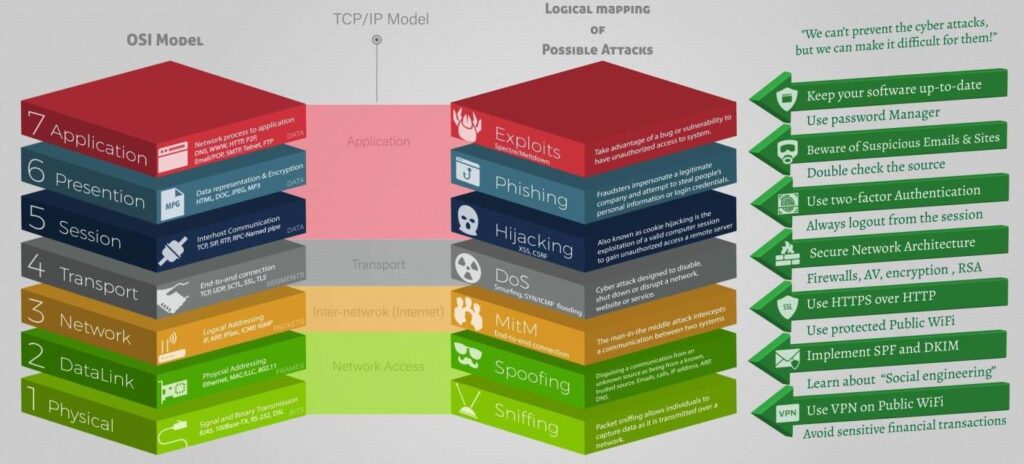
When we think about network security, we often think of it in layers. The most recognised model for this is the Open Systems Interconnection (OSI) model, which divides the network into seven layers to provide Layer 7 Threat Prevention in Cyber Security. The seventh layer, also known as the Application layer, is one of the most critical yet vulnerable layers in this structure. It is where users interact with the network, making it a prime target for cyber attackers. This article will explore the concept of Layer 7 (L7) threats and how to prevent them.
Understanding the OSI Model and Layer 7
Before we delve into L7 threats, it’s crucial to have a basic understanding of the OSI model. This model is a conceptual framework that standardises the functions of a network into seven categories or layers. These are Physical, Data Link, Network, Transport, Session, Presentation, and Application.
Layer 7, or the Application layer, provides the interface for software applications to connect and communicate over the network. It involves protocols that drive end-user interaction with the network, like HTTP for web browsing, SMTP for email, FTP for file transfers, and DNS for domain name resolution.
What are Layer 7 Threats?
Layer 7 threats, also known as application layer attacks, target the user-interface level. They are some of the most common and potentially damaging forms of cyber threats. They encompass several attack vectors, including:
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into trusted websites viewed by users. The script can access sensitive information such as session cookies, enabling identity theft.
- SQL Injection (SQLi): Attackers manipulate a site’s database queries by injecting malicious SQL commands, which can lead to unauthorised data access, modification, or deletion.
- Distributed Denial-of-Service (DDoS) attacks: Here, attackers overload a server with requests, causing it to slow down or crash, denying service to legitimate users.
- Cross-Site Request Forgery (CSRF): Attackers trick a user into executing unwanted actions in a web application in which they’re authenticated, potentially leading to malicious changes on their behalf.
- Zero-day exploits: These are attacks that take advantage of a security vulnerability on the same day that the vulnerability becomes known to the software creator.
Prevention of Layer 7 Threats
Given the diverse range of Layer 7 threats, a multi-faceted approach is required for prevention.
Input Validation
Input validation is a fundamental method for preventing attacks that involve malicious user input, like XSS and SQLi. The idea is to reject input containing dangerous content such as scripts or SQL commands. Using allow-lists (only allowing specified inputs) is generally safer than using block-lists (blocking specified inputs) because attackers can often find a way around block-lists.
Web Application Firewalls (WAFs)
WAFs are a crucial defense tool that protects web applications by monitoring HTTP traffic between the application and the Internet. They can identify and block common L7 threats like XSS, SQLi, CSRF, and DDoS attacks. They often include signature-based detection, blocking known malicious patterns, and anomaly-based detection, identifying unusual behavior.
Regular Patching and Updates
Many L7 threats, especially zero-day exploits, take advantage of vulnerabilities in out-of-date software. Regularly updating and patching your software can help close these vulnerabilities.
User Awareness and Training
Since many L7 threats require some level of user interaction (clicking a link, for example), user awareness is key. Regular training on spotting potential threats can prevent many attacks.
Intrusion Detection/Prevention Systems (IDS/IPS)
These systems monitor network traffic for suspicious activity and issue alerts or block traffic when they detect potential attacks. They can be particularly useful for identifying and mitigating DDoS attacks.
Secure Coding Practices
Implementing secure coding practices is key to developing robust software. Techniques such as code reviews, static code analysis, and dynamic application security testing can help identify and rectify potential vulnerabilities during the development phase.
Conclusion
Layer 7 threats pose a significant challenge to cybersecurity, and their prevention requires a multifaceted approach. Through a combination of robust security tools, regular software updates, secure coding practices, and user awareness, businesses can strengthen their defenses against these sophisticated attacks. While absolute security may be unattainable, the goal should always be to stay one step ahead of potential attackers.
I enjoyed reading your piece and it provided me with a lot of value.
Thank you for your articles. I find them very helpful. Could you help me with something?